Tunnel-less VPN (Group Encrypted Transport)
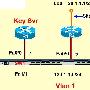 Tunnel-less VPN (Group Encrypted Transport)
Tunnel-less VPN (Group Encrypted Transport)点击查看大图 hostname r1 crypto isakmp policy 10 authentication PRe-share crypto isakmp key cisco add
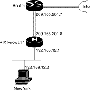 CCIE 实验:VPN Tunnel Network [PIX]
CCIE 实验:VPN Tunnel Network [PIX]文字Configuring PIX Firewall 1 with VPN Tunneling Step 1 Define a host name: ho
(五)site to site vpn的配置(采用rsa-encrypted) 实验网络拓扑: router3662---switch---router1720 3662接口ip:
Decrypt encrypted stored procedures Decrypt encrypted stored procedures http://sea
This SP will decrypt Stored Procedures, Views or Triggers that were encrypted using "with e
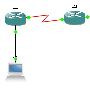 CISCO Tunnel通道的配置说明-应用技巧
CISCO Tunnel通道的配置说明-应用技巧Tunnel通道可以看作是最简单的一种VPN形式,它的参数很简单只要配置Tunnel Source 和 Tunnel Destination两个参数就可以了。 下面用实验来说明一下配置的
病毒名称(中文): 病毒别名: 威胁级别: ★★☆☆☆ 病毒类型: 黑客程序 病毒长
Fedora 9 终于换成了 2.6.25 kernel,2.6.25 支持 ISATAP 方式的 ipv6 tunnel 接入。于是把自己的机器简单配置了一下支持IPV6 1: 保证 ker
Network Working Group G. Zorn Request for Comments: 2868 Cisco Systems, Inc. Updates: RFC2865 D. L
Network Working Group G. Zorn Request for Comments: 2867 Cisco Systems, Inc. Category: Information